71+ pages asymmetric encryption uses choose all that apply 2.8mb explanation in Google Sheet format. Used for digital signatures E. Select all that apply. Asymmetric Cryptography and Digital Signatures. Check also: uses and asymmetric encryption uses choose all that apply Asymmetric encryption Hashing One-Time Pad Symmetric encryption.
The public key is open to everyone. Asymmetric cryptographic algorithms are also known as private key cryptography.
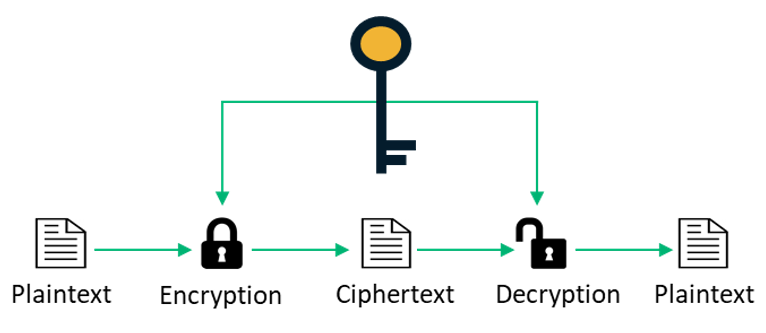
Symmetric Vs Asymmetric Encryption 5 Differences Explained Experts
| Title: Symmetric Vs Asymmetric Encryption 5 Differences Explained Experts Asymmetric Encryption Uses Choose All That Apply |
| Format: Doc |
| Number of Views: 3360+ times |
| Number of Pages: 213+ pages |
| Publication Date: June 2017 |
| Document Size: 1.8mb |
| Read Symmetric Vs Asymmetric Encryption 5 Differences Explained Experts |
 |
Asymmetric encryption is a type of encryption that uses two separates yet mathematically related keys to encrypt and decrypt data.

Within step 2 multiple rounds are performed depending upon the key size. Called public key encryption C. - PGP - GPG - EFS - GNUPG. Choose All That Apply A. The public key encrypts data while its corresponding private key decrypts it. Asymmetric encryption is choose all that apply Answers.

Asymmetric Encryption Public Key Cryptography Video Conferencing
| Title: Asymmetric Encryption Public Key Cryptography Video Conferencing Asymmetric Encryption Uses Choose All That Apply |
| Format: Google Sheet |
| Number of Views: 7184+ times |
| Number of Pages: 189+ pages |
| Publication Date: March 2018 |
| Document Size: 1.7mb |
| Read Asymmetric Encryption Public Key Cryptography Video Conferencing |
 |

Asymmetric Cryptography An Overview Sciencedirect Topics
| Title: Asymmetric Cryptography An Overview Sciencedirect Topics Asymmetric Encryption Uses Choose All That Apply |
| Format: Doc |
| Number of Views: 6209+ times |
| Number of Pages: 199+ pages |
| Publication Date: May 2018 |
| Document Size: 725kb |
| Read Asymmetric Cryptography An Overview Sciencedirect Topics |
 |

Implement Symmetric And Asymmetric Cryptography Algorithms With C
| Title: Implement Symmetric And Asymmetric Cryptography Algorithms With C Asymmetric Encryption Uses Choose All That Apply |
| Format: PDF |
| Number of Views: 8203+ times |
| Number of Pages: 208+ pages |
| Publication Date: August 2017 |
| Document Size: 2.2mb |
| Read Implement Symmetric And Asymmetric Cryptography Algorithms With C |
 |
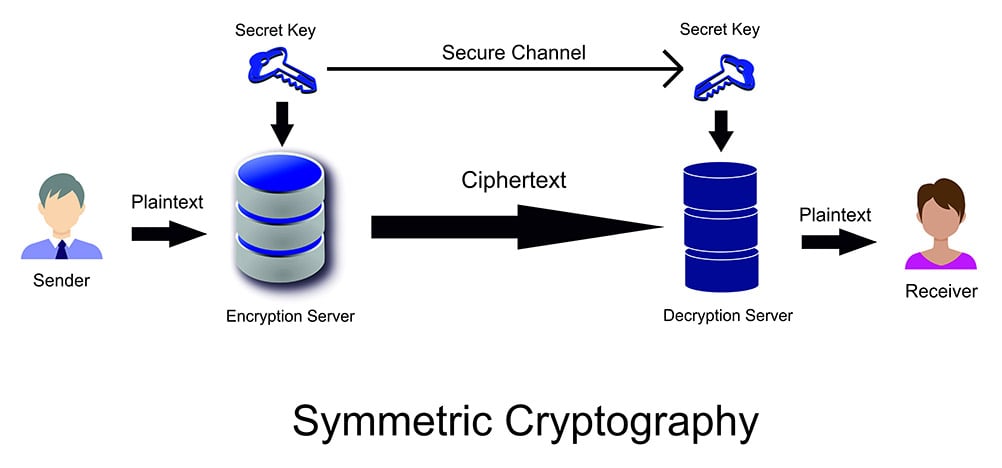
Symmetric Vs Asymmetric Encryption What S The Difference
| Title: Symmetric Vs Asymmetric Encryption What S The Difference Asymmetric Encryption Uses Choose All That Apply |
| Format: Doc |
| Number of Views: 3070+ times |
| Number of Pages: 342+ pages |
| Publication Date: September 2018 |
| Document Size: 2.1mb |
| Read Symmetric Vs Asymmetric Encryption What S The Difference |
 |
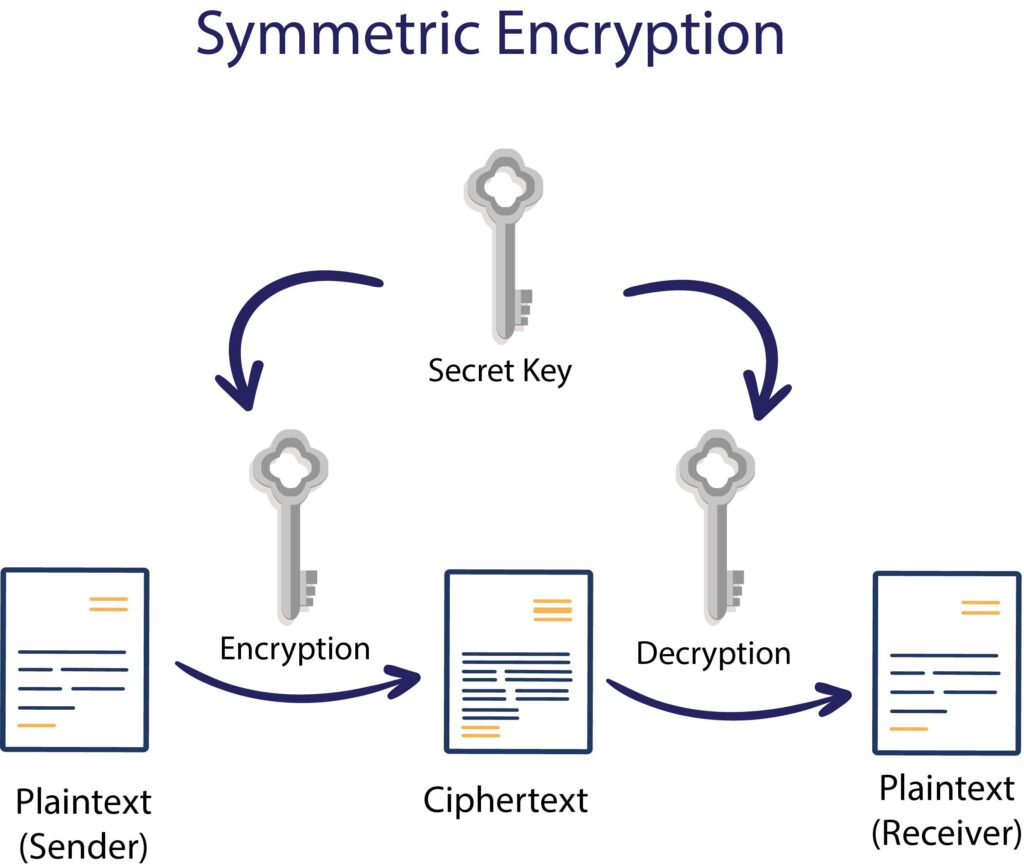
What Are Encryption Protocols And How Do They Work Encryption Consulting
| Title: What Are Encryption Protocols And How Do They Work Encryption Consulting Asymmetric Encryption Uses Choose All That Apply |
| Format: Google Sheet |
| Number of Views: 3150+ times |
| Number of Pages: 144+ pages |
| Publication Date: June 2020 |
| Document Size: 1.4mb |
| Read What Are Encryption Protocols And How Do They Work Encryption Consulting |
 |
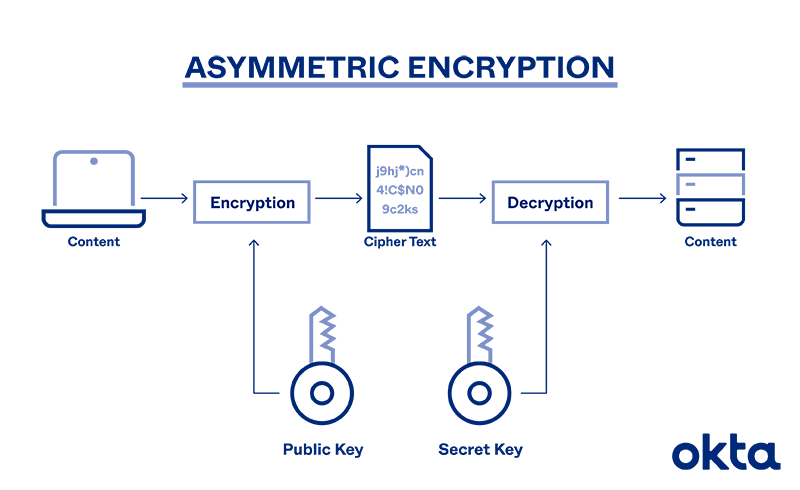
Asymmetric Encryption Definition Architecture Usage Okta
| Title: Asymmetric Encryption Definition Architecture Usage Okta Asymmetric Encryption Uses Choose All That Apply |
| Format: Doc |
| Number of Views: 7133+ times |
| Number of Pages: 11+ pages |
| Publication Date: June 2021 |
| Document Size: 1.7mb |
| Read Asymmetric Encryption Definition Architecture Usage Okta |
 |
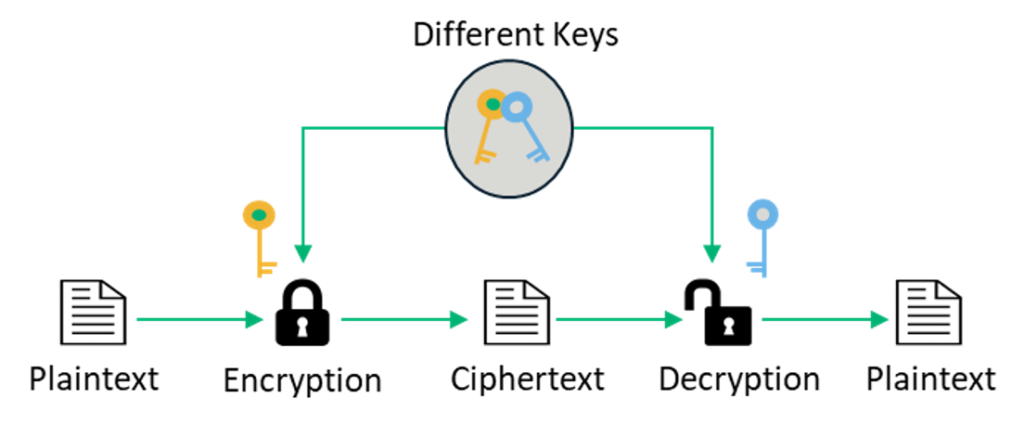
Symmetric Vs Asymmetric Encryption 5 Differences Explained Experts
| Title: Symmetric Vs Asymmetric Encryption 5 Differences Explained Experts Asymmetric Encryption Uses Choose All That Apply |
| Format: PDF |
| Number of Views: 7136+ times |
| Number of Pages: 326+ pages |
| Publication Date: September 2019 |
| Document Size: 1.5mb |
| Read Symmetric Vs Asymmetric Encryption 5 Differences Explained Experts |
 |

What Types Of Encryption Are There Ico
| Title: What Types Of Encryption Are There Ico Asymmetric Encryption Uses Choose All That Apply |
| Format: Google Sheet |
| Number of Views: 7133+ times |
| Number of Pages: 129+ pages |
| Publication Date: May 2020 |
| Document Size: 725kb |
| Read What Types Of Encryption Are There Ico |
 |

Types Of Encryption Symmetric Or Asymmetric Rsa Or Aes The Missing Report
| Title: Types Of Encryption Symmetric Or Asymmetric Rsa Or Aes The Missing Report Asymmetric Encryption Uses Choose All That Apply |
| Format: Doc |
| Number of Views: 8175+ times |
| Number of Pages: 284+ pages |
| Publication Date: May 2020 |
| Document Size: 725kb |
| Read Types Of Encryption Symmetric Or Asymmetric Rsa Or Aes The Missing Report |
 |

Si110 Asymmetric Public Key Cryptography
| Title: Si110 Asymmetric Public Key Cryptography Asymmetric Encryption Uses Choose All That Apply |
| Format: Google Sheet |
| Number of Views: 3400+ times |
| Number of Pages: 231+ pages |
| Publication Date: July 2017 |
| Document Size: 1.2mb |
| Read Si110 Asymmetric Public Key Cryptography |
 |
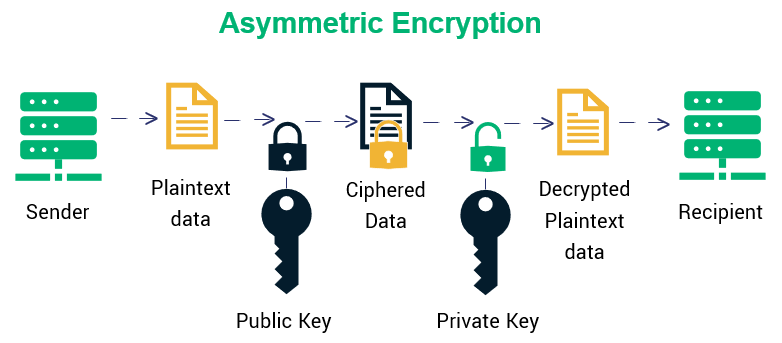
Types Of Encryption What To Know About Symmetric Vs Asymmetric Encryption Infosec Insights
| Title: Types Of Encryption What To Know About Symmetric Vs Asymmetric Encryption Infosec Insights Asymmetric Encryption Uses Choose All That Apply |
| Format: PDF |
| Number of Views: 7177+ times |
| Number of Pages: 22+ pages |
| Publication Date: October 2017 |
| Document Size: 5mb |
| Read Types Of Encryption What To Know About Symmetric Vs Asymmetric Encryption Infosec Insights |
 |
TLS or SSL the protocol that makes HTTPS possible relies on asymmetric encryption. What widely used commercial asymmetric cryptography software can be used for encrypting files and email messages. A session key is a one-time-use symmetric key that is used for encryption and decryption.
Here is all you have to to know about asymmetric encryption uses choose all that apply Steganography is a hashing technique C. A Copy Of The Symmetric Encryption Key Is Stored Within The File Metadata And Asymmetrically Encrypted With Your Public Key C. It is a type of security through obscurity. Si110 asymmetric public key cryptography symmetric vs asymmetric encryption what s the difference asymmetric encryption public key cryptography video conferencing asymmetric cryptography an overview sciencedirect topics implement symmetric and asymmetric cryptography algorithms with c what are encryption protocols and how do they work encryption consulting Select all that apply.
0 Comments